Taking the Work out of Workflows – Part 1: Threat Management
After the network has been turned inside out by an event such as an unexpected increase in remote working, an organization becomes more vulnerable to successful penetration. When faced with a potentially serious threat, it is obvious that we need to take the fewest steps and spend the least amount of time possible to efficiently and quickly move from detection to response. As obvious as that seems, many are learning through experience that existing tools and processes don’t align well at all with this desired state.
Why? In many cases, it is simply a matter of needing to collect large volumes of raw data without having a corresponding ability to extract clear concise information that can be efficiently transformed into answers and actions.
The approach that some take is to summarize those large volumes of raw data into metadata. While there are certainly situations where this is quite helpful, there are also times when literally every bit of information is needed in order to recreate an event or understand the impact. So, where does that leave us? How do we bring the actionable information to the surface without discarding the critical details that might be needed for forensic analysis?
Let’s look at an example of the role the right workflow can play in addressing this challenge.
Step 1: Detection
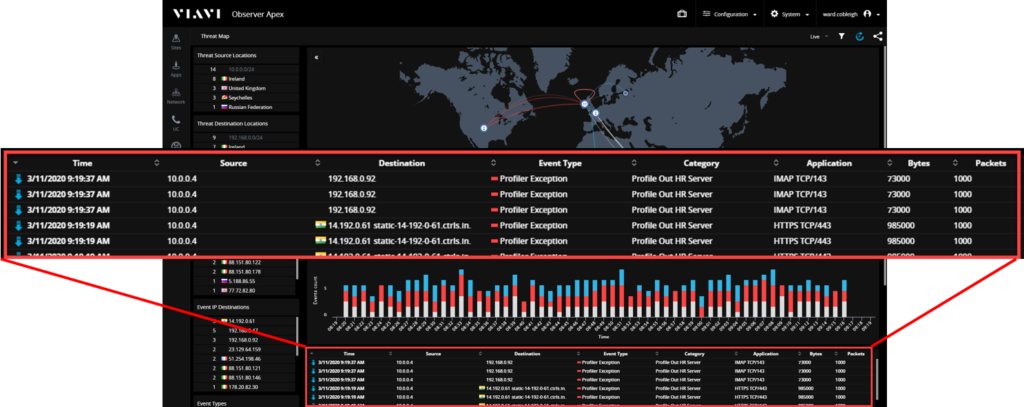
Knowing how our hosts or devices ought to behave should allow us to quickly see when they aren’t behaving that way. In this example, from a top-level threat map we can see that we have an HR server that has suddenly started having conversations that aren’t part of its standard behavior profile.
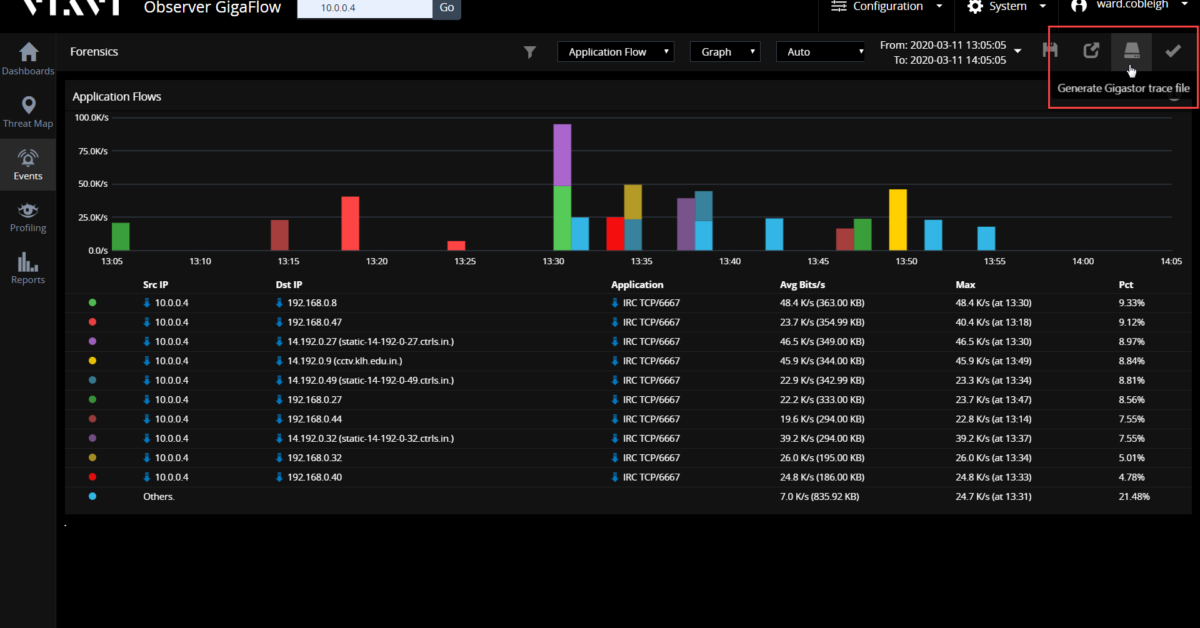
Step 2: Focus
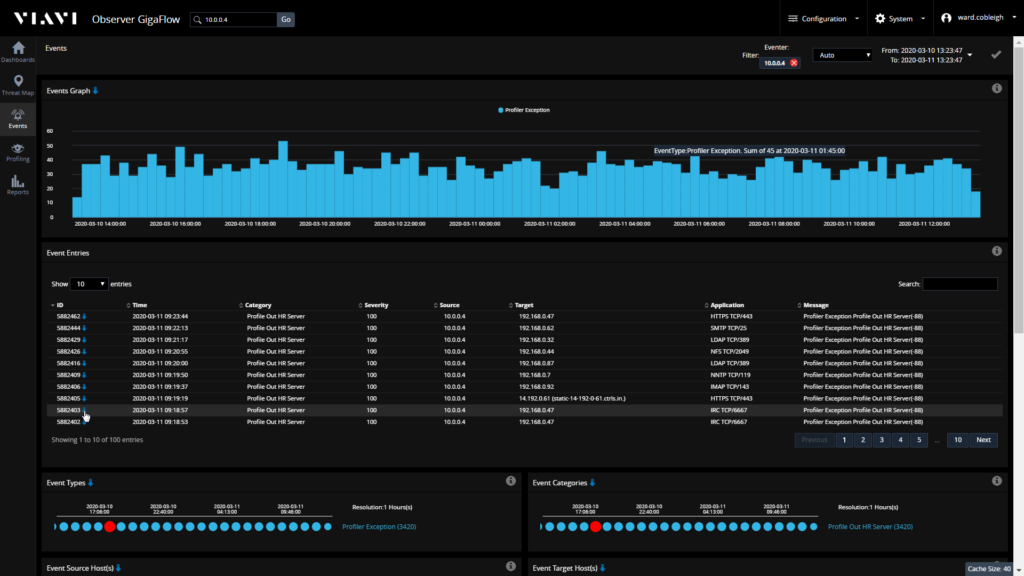
Our attention quickly shifts to this one host – what conversations is this server having that are atypical? Looking at the events that describe the exceptions to the expected behavior, we see how often the unexpected conversations are occurring and more details on who our device is talking to and the types of communications that are taking place.
In this example, let’s say that one specific item is of particular concern; the traffic on TCP port 6667. Who is our HR server talking to and what, exactly, has been transmitted?
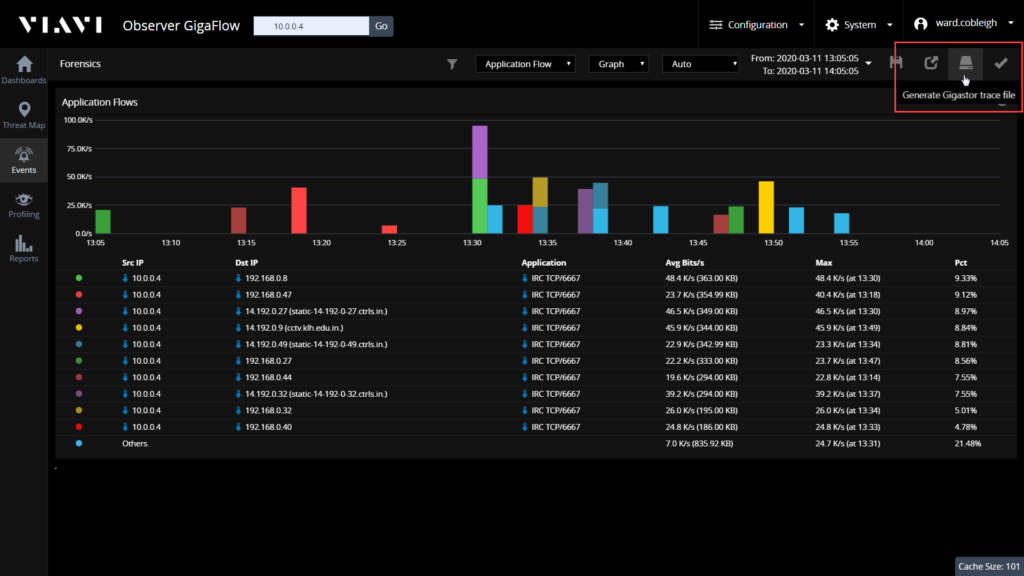
Step 3: Forensics
Our forensic analysis details every single conversation that the server had using that port, the time period over which those conversations took place, and the amount of data that was moved. An export option gives us the ability to extract the packets that provide every bit of information that moved across the wire. If an exfiltration has taken place, we’ll have the evidence we need to document precisely what was compromised.
What have we illustrated in this example?
- The importance of automatically identifying, extracting, and presenting actionable information – our HR server is talking to someone it doesn’t usually talk to, we should figure out what’s going on.
- The value of marrying that actionable information with simple, efficient workflow – we went from detection to forensic-level analysis in three steps.
- Ease of use – virtually any member of our team could see and understand the issue and literally go from the map to the packets. Now the security analyst or device/service owner has a clear description of the issue and only the raw data needed for resolution.
- The value of seamlessly unifying flow data (NetFlow, IPFIX, etc.) with wire data (the packets).
You may already have all the data. Maybe it’s time to revisit how to best put it to work. The right workflow will have less work and more flow. Take a look at the latest release of VIAVI Observer Platform and discover how to make sure you have the right data available at your fingertips.
Additional Threat Management resources: