The last question you want to hear after a fire in your building is, ‘We have a backup …. right?’ Similarly, the last question you want to hear after a supply-chain attack, like the recent Sunburst catastrophe, is ‘We have what we need to determine if we were breached…right?” Remediation for this type of event […]
Category Archives NPMD
For those organizations pursuing an aggressive digital transformation, heightened network visibility and control has become a critical success factor. For less aggressive digital transformers, the COVID-19 experience has served notice that more timely and precise monitoring and management of the network is required both during and after the pandemic. Here at IDC, we’ve been monitoring […]
We are excited and very proud to share that we have been recognized as Gartner Peer Insights Customers’ Choice 2020, with a rating of 4.9 out of 5.0. Find out more and download the complementary 2020 Gartner Market Guide. We take huge pride in this distinction, as it is based on reviews by VIAVI customers. […]
Financial institutions have felt the dramatic impact of the new working paradigm and find it is critical for employees to use Virtual Private Networks (VPNs) whenever possible and for IT to manage them effectively. The sheer volume of high-speed financial transactions every minute means that there is a need to ensure confidentiality, integrity, and availability […]
Travel and other restrictions are preventing us from meeting you in person, but we’ve come up with the next best thing – our unique virtual roadshow! This is not just another webinar dressed up as an event – we have been working hard to bring you an online event with everything you’d expect from an […]
In the first half of 2020, IT teams around the globe rapidly responded to unprecedented change, threw the rule book out the window (in many cases), and found innovative and in some cases unorthodox ways to keep the business running while transitioning into some ill-defined “new normal”. This upheaval created opportunities that cybercriminals were eager […]
Ten months ago, we had a nice chat about the importance of having a simple, reliable means of understanding the end-user experience and efficiently identifying problem domains. While much has changed since then, it appears that we still have a score to settle when it comes to end-user experience management. VIAVI Solutions has just released […]
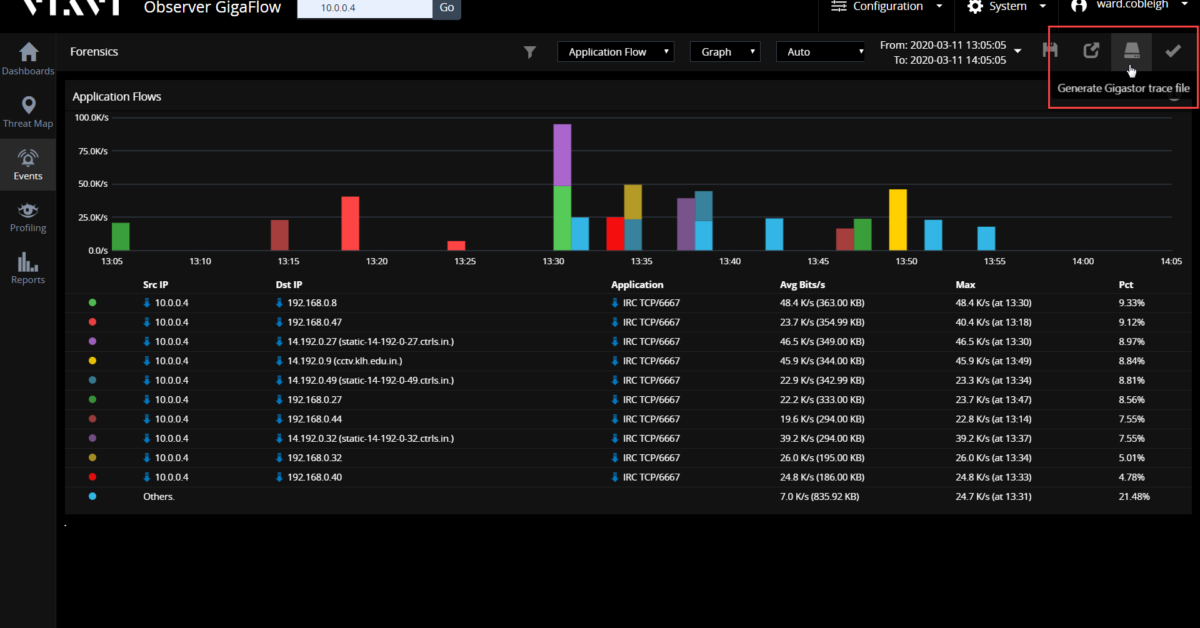
When faced with validating and resolving a performance problem with a complex application, we need complete visibility into how the various components of the application are performing. The way most vendors approach this need is to deliver Key Performance Indicators (KPIs) that describe how each of the various elements of the system is performing. Having […]
One title that is in no danger of appearing on a list of “Most Boring Jobs” is that of Enterprise IT Director (or its equivalent). In the 2010s, IT teams had to contend with increasing adoption of advanced network technologies such as hybrid cloud or SDN. They became more and more involved with security investigations, […]
After the network has been turned inside out by an event such as an unexpected increase in remote working, an organization becomes more vulnerable to successful penetration. When faced with a potentially serious threat, it is obvious that we need to take the fewest steps and spend the least amount of time possible to efficiently […]