Container Deployment Security Validation

Virtual environments have been critical for many of us over the past year. The office as a physical space – not just for employees but a place to host servers and hardware – is diminishing in importance. Employees have been able to access applications and collaborative working tools wherever they’ve been working, reducing our reliance on the physical office space. Enterprises have been able to access and deploy new applications quickly and easily. Developers meanwhile have been able to develop, enhance, and launch applications for enterprises far more rapidly than even a few years ago. These developments are all thanks to two Cs: the Container and the Cloud.
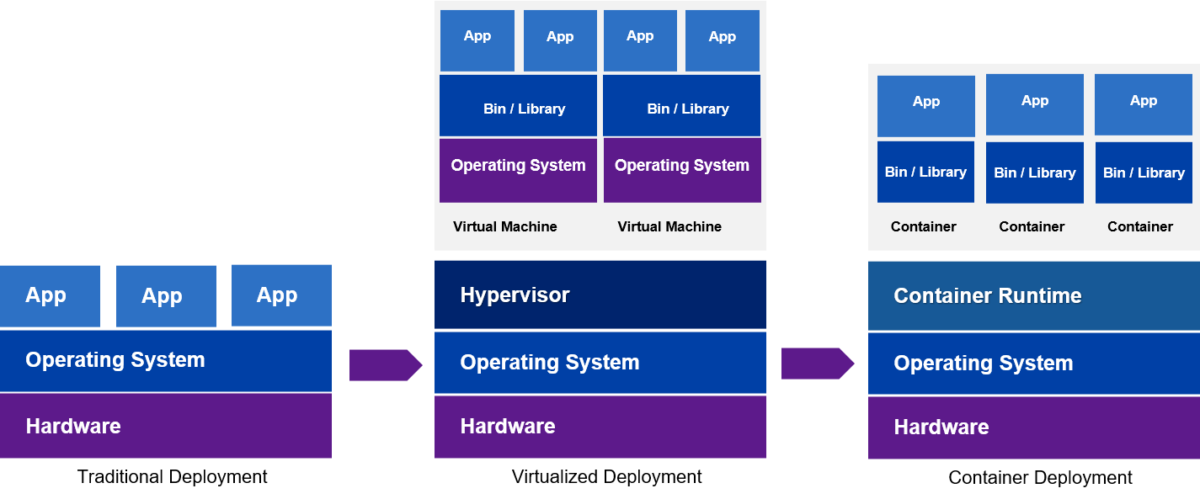
 Instead of being hosted on servers, enterprise applications are rapidly migrating to highly scalable and agile cloud native applications that are infrastructure agnostic. Containers allow for software applications to be packaged up into standalone units and moved across these different computing infrastructures. Applications can also be split into smaller elements – microservices – giving developers more flexibility if they want to make changes and improvements to apps. They are often orchestrated by Kubernetes – an open-source system for automating computer app deployment – enabling scaling horizontally based on different workloads.
Instead of being hosted on servers, enterprise applications are rapidly migrating to highly scalable and agile cloud native applications that are infrastructure agnostic. Containers allow for software applications to be packaged up into standalone units and moved across these different computing infrastructures. Applications can also be split into smaller elements – microservices – giving developers more flexibility if they want to make changes and improvements to apps. They are often orchestrated by Kubernetes – an open-source system for automating computer app deployment – enabling scaling horizontally based on different workloads.
Benefits of Cloud and Containerization
There are huge benefits to this; containers can be moved across different cloud environments and application development is faster and more agile. Security is also improved as applications are isolated from the host system and from each other. This is good for developers and good for their enterprise customers.
It’s not surprising therefore that Gartner predicts that by 2022, more than 75% of global organizations will be running containerized applications in production, which is a significant increase from fewer than 30% today. These deployments are expected to happen in public cloud infrastructures instead of on-premise deployments. Today, around 10% of enterprises have already moved their application deployment completely into the public cloud infrastructures.
Testing Security in Containerized Environments
As with any change or addition to a network, testing security ahead of deployment is critical. This must include testing firewalls and Next Generation Firewalls (NGFW). Like the applications themselves, NGFW are also being evolved to be deployed in container clusters. And it’s here that problems can arise.
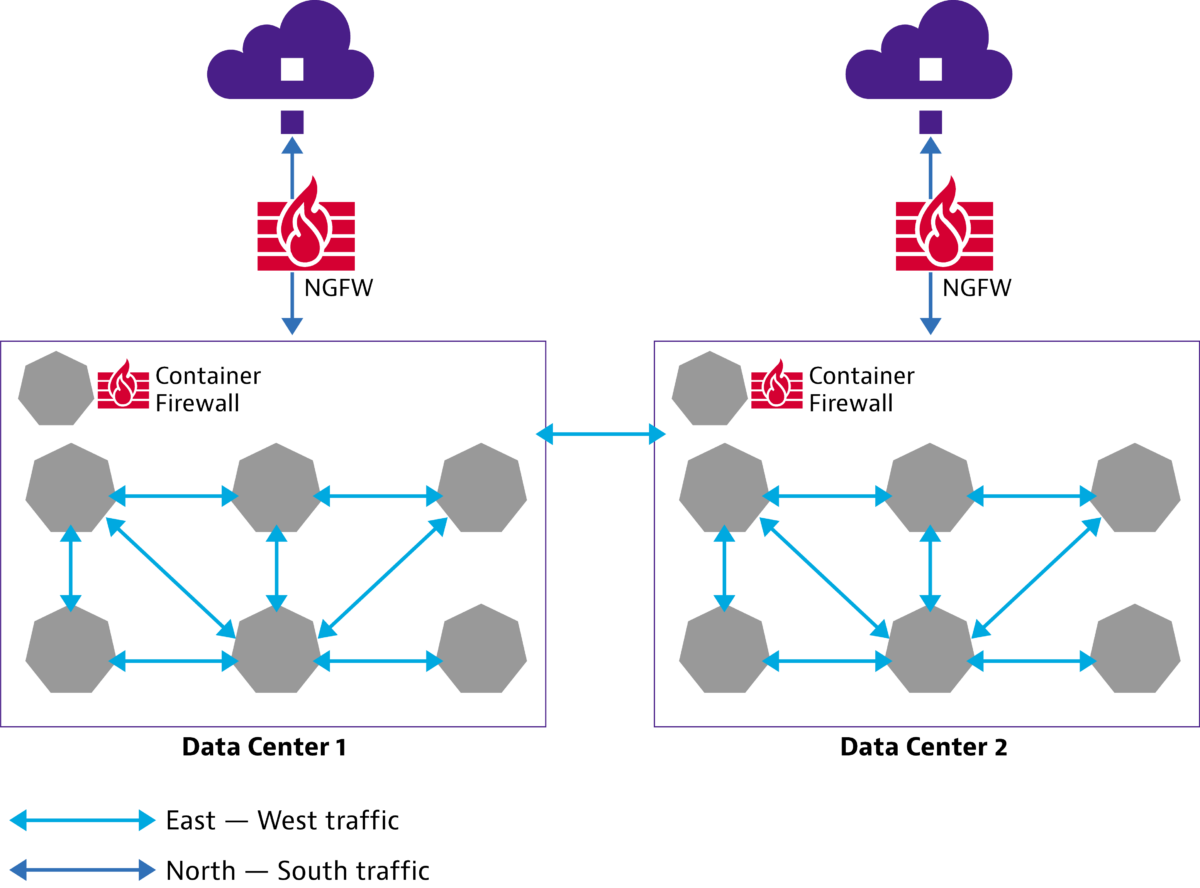
Container based microservices are typically ephemeral workloads that are constantly started, stopped and updated through CI/CD pipelines. As containers scale horizontally and faster, there is an explosion of the east-west traffic, or what is called internal traffic, within the container clusters. The traditional firewalls and NGFWs that offer protection at the edge for external/north-south traffic are unsuited for securing container traffic as they do not ‘see’ them.
A such, container security requires a different approach. A container firewall offers east-west as well north-south protection in a cloud-native environment. The solution? Think cloud native: you need a cloud native firewall to protect cloud native container traffic, and similarly, you require a cloud native test tool – with visibility to the internal cloud network – to validate cloud native firewall solutions, by emulating east-west pod traffic.
VIAVI Scores a First with TeraVM
Our TeraVM product is the industry’s first commercial tool that offers a cloud native testing solution natively integrated with Kubernetes. Containerized TeraVM is deployable in public cloud managed Kubernetes services such as Google Kubernetes Engine (GKE) and Amazon Elastic Kubernetes Service (EKS).
A TeraVM test bed is a group of TeraVM components that generate IP test traffic with customizable traffic profiles. Users can easily deploy the tool using Helm Package Manager in Kubernetes environments hosted on the public cloud, and it can be deployed and traffic generated without any third-party network plugins. TeraVM supports a wide variety of voice, video and data traffic profiles to be emulated in the container network. Traffic is generated between TeraVM client and Server pods using Service IPs and capacity of test bed can be scaled easily by deploying more TeraVM pods. This allows users to validate containerized firewalls for TLS Traffic inspection, URL filtering and custom threat generation.
We’ve grown accustomed to virtual environments and cloud-native applications, and the benefits they bring to developers, enterprises, and end users. It makes sense that we take the same approach to network and security testing – using tool a that offers a cloud native testing solution, natively integrated with Kubernetes.
Find out more about the benefits of using the containerized TeraVM security validation test tool.




