A generation ago, adding more gauges, dials, and displays to car dashboards was all the rage, with data-hungry drivers anxiously monitoring vehicle performance and efficiency from the comfort of the driver’s seat. Today, we have come full circle, with unified displays presenting more information while distilling it in a way that lets us keep our […]
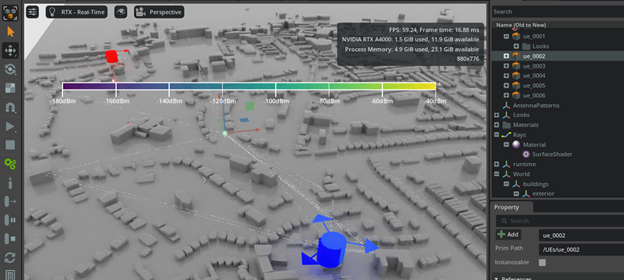
At the NVIDIA GTC conference, VIAVI announced it is expanding its TeraVM AI RAN Scenario Generator (AI RSG) product by integrating it with the NVIDIA Aerial Omniverse Digital Twin (AODT). The integration enables realistic and detailed radio access network (RAN) simulations, supporting network equipment manufacturers to leverage network data and AI/ML to optimize network operations. […]
Looking to secure NTIA’s NOFO 3 funding? Partnering with VIAVI can set your proposal apart! As a trusted leader in test, automation, and optimization, and the only test company awarded funding under NOFO 1, VIAVI brings unmatched expertise to help you accelerate Open RAN deployments and network performance. Why VIAVI Is Your Ultimate Partner AI-Powered […]
VIAVI is excited to collaborate with the AI-RAN Alliance, a trailblazer in advancing AI-native Radio Access Networks (RAN), to establish the first AI-RAN Alliance-endorsed lab. This strategic initiative is set to elevate the research and testing capabilities in the telecommunications industry, with a particular focus on integrating artificial intelligence into RAN technologies. AI-RAN (Artificial Intelligence-powered […]
The UEC Stack will mark a major evolution in Ethernet, integrating scalability, low latency, and congestion control for AI and HPC data centers. However, traditional testing won’t be enough. Learn why new assurance models, multi-KPI validation, and real-world traffic modeling will be essential for success—and what effective testing strategies involve. Significant leap forward in networking […]
224G SERDES is a high-speed interface technology that underpins next-generation 1.6Tb links. Getting 224G signals from the ASIC to the interconnect and beyond remains a key challenge for the deployment and scaling of 1.6Tb. Each 1.6Tb link uses 8 lanes of 224G signaling. For Ethernet, this actually runs at 212.5 Gb/s, which includes some overhead […]
Mobile World Congress (MWC) Barcelona is almost here again. Last year saw several major announcements on the evolution to 6G, including a notable joint shared-principles statement from 10 countries announcing their intention to “support open, free, global, interoperable, reliable, resilient, and secure connectivity.” As a trusted partner in network test, automation, and optimization for over […]
Network visibility is enhanced through the time-stamped logs, performance metrics, and end-to-end traces collectively known as telemetry data. Each unique data source provides valuable clues that help IT teams and network engineers resolve issues and maintain performance standards, both locally and in the cloud. When these discreet lanes of information converge with comprehensive and inciteful […]
As digital technologies advance and consumer demands shift, the global telecommunications industry is rapidly undergoing a transformation. Faster networks and lower latencies are required to support emerging technologies such as IoT networks/systems, AI and cloud computing. As such, telcos are evolving to resemble technology companies, with a focus that extends beyond what a traditional telco […]
In aviation, “visibility” determines how far pilots can see important landmarks—mountains, runways, or other aircraft—to navigate safely, even without advanced instruments. Similarly, network visibility empowers IT teams to clearly understand performance baselines, swiftly pinpoint issues, and mitigate risks before they escalate. However, the reliable, time-tested resources and metrics traditionally used to monitor traffic, performance, and […]