Taming the Risks of SD-WAN: Evolving SD-WAN Security and SASE Architecture

Secure Access Secure Edge (SASE) represents an evolutionary step for SD-WAN vendors to enhance SD-WAN security in the multi-cloud environment. Learn why a comprehensive test and validation strategy is essential to manage SD-WAN security effectively.
SD-WANs are commonly virtualized and rely heavily on the public Internet, along with a range of private WAN connections. Managing security for SD-WAN is a moving target and a balancing act. The need for secure SD-WAN services has been driven by systemic changes in how enterprise applications and data are delivered, and dramatic shifts in the workplace.
In response, SASE (developed by Gartner in 2019), is redefining SD-WAN security by removing the physical perimeter that has governed security for generations, especially in the enterprise environment. SASE is addressing enterprise security as two major trends unfold. One is a long-term trend where applications and data are moving from the data center into the cloud. That’s been happening for over a decade. Analysts estimate that over half the workloads have already been migrated to public clouds. Simultaneously, the workforce was forced to move from the campus or office into a work-from-home (WFH), or a work-from-anywhere environment. That is having dramatic implications.
Both trends were accelerated by Covid-19 in 2020, and the WFH environment in particular creates a problem for enterprise CSOs who are attempting to maintain order and security, even though the network is not under their control. Home networks are particularly troubling to CIO/CSOs, which may not be readily managed by IT and expose a myriad of new vulnerabilities.
SASE is a distributed security architecture envisioned to address the cloud-centric world. Instead of assuming a physical perimeter, SASE up-levels the protection to secure users and applications as opposed to subnetworks and IP resources.
In the SASE architecture, security functions are deployed into the cloud, and specifically at the edge. Users request access via connections to the cloud, no matter where in the world they are located. Once access is granted, the user’s identity, role, and context is considered prior to be permitted to access applications and data. Should the context change, access privileges may be changed as well. All such decisions are made independent of the physical location, network, etc.
SASE is predicated on a companion technology called Zero Trust and Zero Trust Network Access (ZTNA). Zero Trust eliminates the notion of trust, necessitating that access must be granted for each application transaction. In other words, every time something is accessed, both inside and outside an organization’s perimeter, ZTNA dynamically assesses whether that user has the privileges, the context is appropriate, as their identity is authenticated, and whether they have vetted access to the specific data requested.
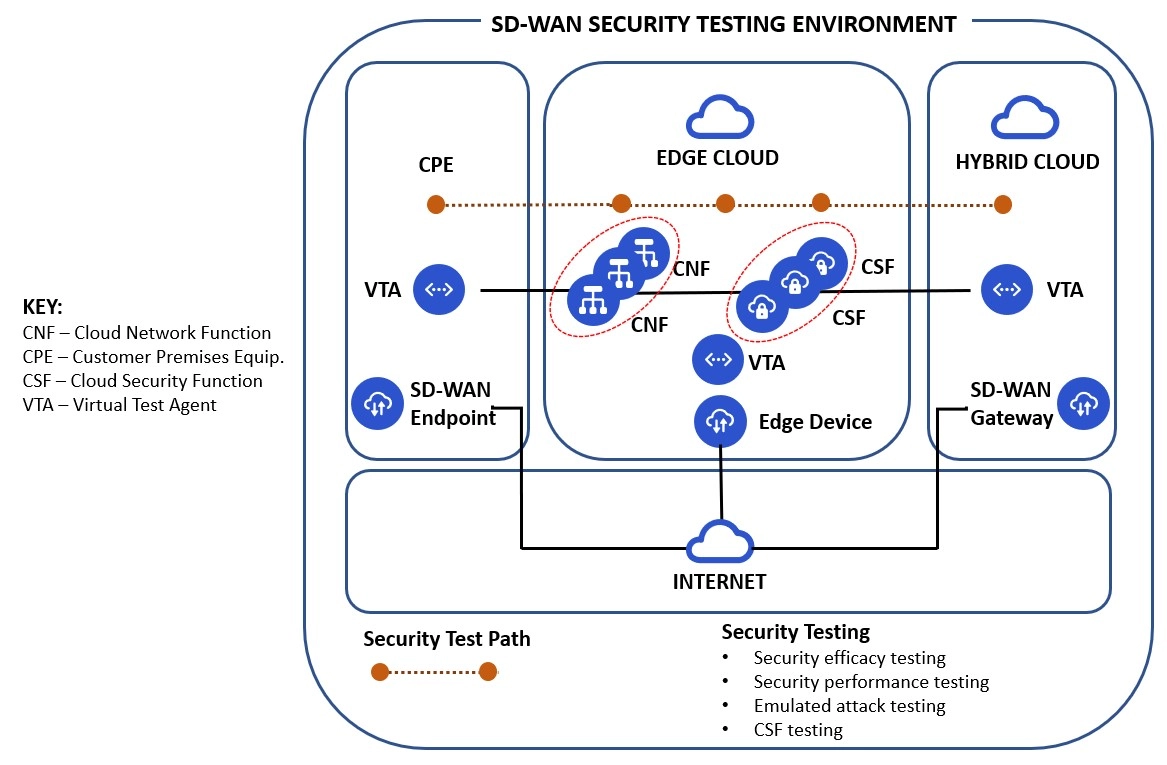
“A sound security testing strategy and capability that comprehensively addresses all the layers is crucial for SD-WAN success. This approach must strike the proper balance between performance impact and security efficacy.”
Empowering the realization of SD-WAN’s promise
SD-WAN ushers in a new era of cloud-based services, which tailor the network to the application demands. However, migration to the cloud incurs challenges of reliable interoperability and inherent inefficiencies. This includes new risks and vulnerabilities as the potential attack surface increases dramatically with an explosion in endpoints and increased use of publicly accessible networks. Taming the complexity of SD-WAN services is further complicated by the virtualization of SD-WAN endpoints and controllers, which introduce a new set of challenges. Any organization attempting to address these complexities on their own, without a deep bench of expertise and technology capabilities, face serious challenges. Having a vendor-neutral partner to tame the risks of SD-WAN is essential to success.


