TestCloud: Staying a Step Ahead of Danger with Continuous Intelligence

Learn how to automate continuous zero-day threat vector testing with TestCloud and get beyond new threats such as Log4J and Spring4Shell.
Organizations face constant and growing challenges in defending against increasingly sophisticated cyber attacks, ranging from ransomware to software supply chain attacks, malware, application exploits, and command and control bots.
The cybersecurity risks are ever-present and constantly evolving. Attackers have a plethora of known Common Vulnerabilities and Exposures (CVEs) and unknown zero-day techniques such as Log4j and Spring4Shell that are setting off broadscale panic. According to the MIT Technology Review, 2021 was a record-breaker for zero-day threats with at least 66 identified instances — twice that of 2020.
The good news is that the world we live in is becoming hyper-vigilant and quick to share pertinent information about the latest threat vectors with the larger community. In addition, organizations and developers are reacting quickly to update their software and applications against these emerging vulnerabilities.
However, it may not always be possible to upgrade and patch the code or take more time to implement the upgrades. In those instances, IT organizations will need to place security controls such as NGFW, IPS, or WAF in front of the vulnerable servers and applications to prevent attacks from getting into the network.
Staying ahead with continuous intelligence
Continuously providing newly found and zero-day threat vector emulation capabilities and makes them automatically available for testing via TestCloud™ content subscription, with thousands of malware and exploit propagation samples for an extensive test coverage. We have a proven track record of having threat samples available for security efficacy validation of zero-day vectors within days of the first incidence report. This in turn enables organizations to run these emulated attacks against their NGFW or WAF to validate whether their security infrastructures are updated to protect against the latest threats.
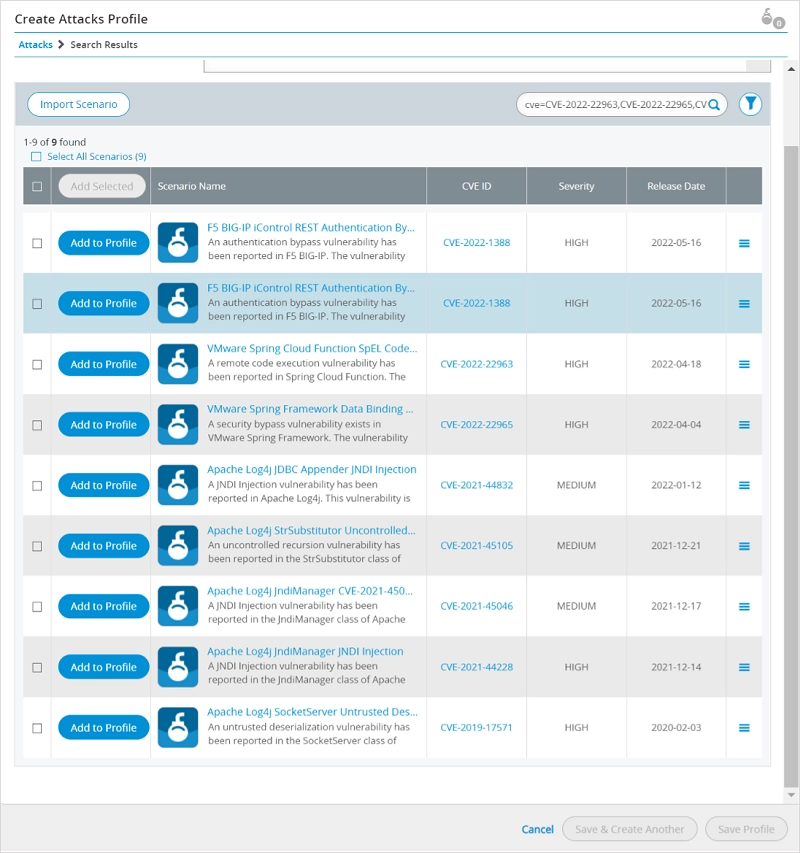
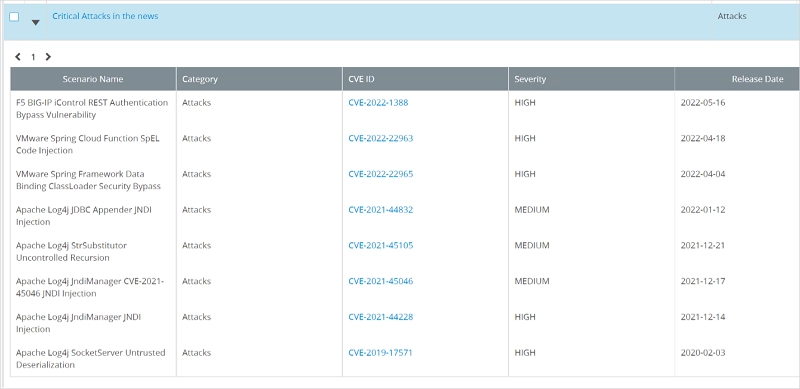
As enterprise IT environments become increasingly complex, the attack surface continues to grow rapidly due to continued trends of remote work, work from home, cloud services, and bring your own device (BYOD) policies, which drives a need to provide broad security coverage over increasingly complex hybrid network architectures.

